Ethereum & DeFi: How dForce allegedly ‘copied’ other projects’ codes

DeFi is a budding ecosystem with a bright future. Some projects in the ecosystem are promising and are better alternatives to the ones in traditional finance. The growth of this ecosystem has also been staggering. Regardless of that, with a number of exploits DeFi does have a lingering problem that only time and thorough coding can solve. Due to these issues, the growth of DeFi is bottlenecked.
One of the recently affected protocols was a lending platform, “Lendforce.me,” wherein the attacker managed to siphon $25 million. Mindao Yang, Founder of the “dForce foundation” that supports Lendf.me, stated in a blog post that the affected users, included him and the co-founder, among other people.
“This attack was my failure. While I did not execute it, I should have anticipated it and taken actions to prevent it. My heart goes out to everyone harmed, and I will do everything in my power to make this right. I sincerely apologize to our users, to our new investors, and to my team for letting them down.”
Interestingly enough, 48 hours later, the stolen funds were returned by the attacker. A few days later, Yang posted a blog on how the recovered funds were in a cold wallet and will be distributed to the users. Although the funds were recovered and things returned to normal at dForce, the figurative “skeletons” in dForce’s closets were discovered that day.
What lies beneath?
Robert Leshner, Founder of Compound Finance, another popular lending platform on DeFi, alleged in a tweet that Lendf.me had copied Compound’s smart contract code.
Lesher added,
“If a project doesn’t have the expertise to develop it’s own smart contracts, and instead steals and redeploys somebody else’s copyrighted code, it’s a sign that they don’t have the capacity or intention to consider security. Hope developers & users learn from the Lendf.Me hack.”
DeFi’s biggest strength is also its greatest weakness. There is no central authority to assess the risk and hence, the smart contracts themselves act as a counterparty aka the last line of defense. Without proper vetting of the code, the smart contract and the protocol are likely to fail due to bugs that can be exploited. Over the last few months, it has been clear that the DeFi protocol needs a closer look. Take, for example, the dYdX protocol, which also suffered two successive hacks and lost a total of $900,000 due to an exploit in the code.
Hence, it is clear that DeFi is in its infancy. In theory, DeFi could be revolutionary, however, the security aspect seems to be an afterthought, hence, this is hindering investors from taking serious positions in the ecosystem. Multicoin Capital’s Kyle Samani summarized it aptly in a webinar as he explained that the current interest rates on DeFi lending networks do not justify the risks.
“It wouldn’t be meaningful to our portfolio, so it just wasn’t worth the time”
Further, Samani added that DeFi’s growth challenges are more fundamental in nature and that “crypto-collateralized loans aren’t interesting beyond the bounds of existing Ethereum investors.”
Regardless, some investors are optimistic about the ecosystem. The dForce foundation that maintains two protocols, lendf.me and USDx, had raised $1.5 million in a seed round led by Multicoin Capital and joined by Huobi Capital and CMB International (CMBI), a few days before the hack.
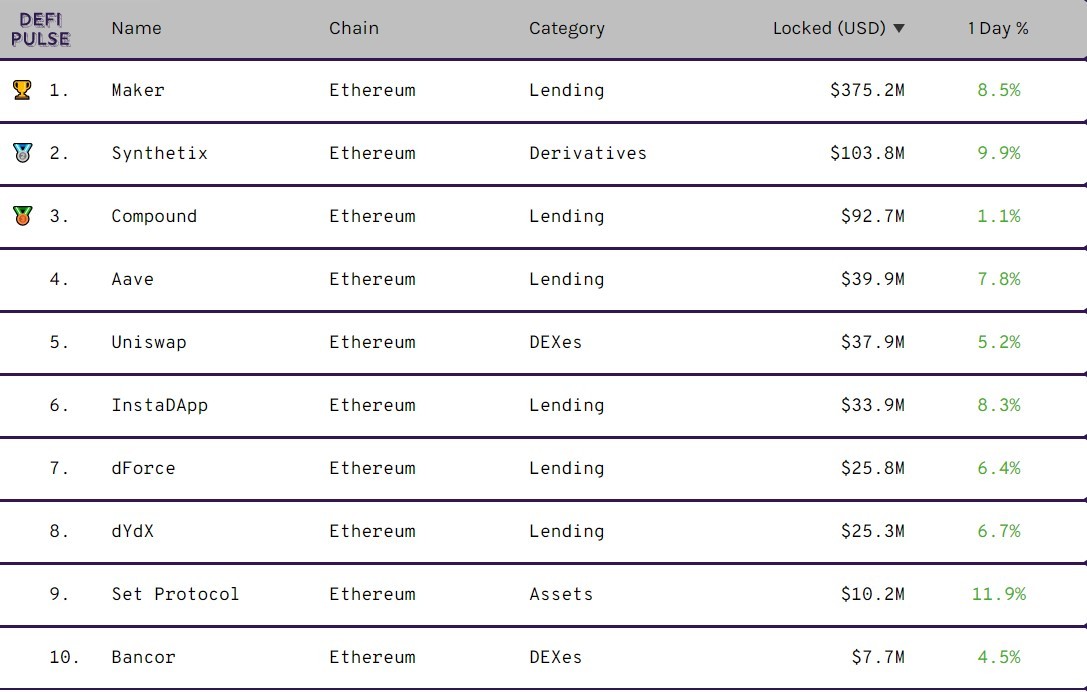
April 16 – Source: DeFi Pulse
dForce was ranked the 7th largest protocol in the DeFi ecosystem with over $25.8 million locked. Things looked normal for dForce as even investors were willing to invest millions in the protocol that allegedly copied the codes of other platforms.
Although Rober Leshner alleged that Lendf.me had copied Compound’s codes, he declined to further comment on the matter when contacted. Additionally, a Twitter user with a screen name “DefiMoon” posted a screenshot of a Telegram group that pointed out that Compound’s legal team was “going after them [lendf.me]” and anyone that integrated the protocol.
Speaking to AMBCrypto, Andre Cronje, DeFi Architect at Ethereum, confirmed that compound was legally going after Lendf.me for copying the code, but added lendf.me “were also working on their own version.”
Advising people who are involved in building DeFi projects, Cronje said,
“Unless you have funding to pay for security audits, or come from a security background yourself, don’t try, you will lose people’s money”
To make matters worse, the code for the second protocol that dForce controls – synthetic stablecoin platform [USDx], was also allegedly stolen. Speaking to AMBCrypto, Kava’s CEO Brian Kerr confirmed the matter. He said,
“dForce also stole Kava’s USDX token name and ticker – despite us announcing our token many months before they even had a platform. Generally it’s normal and acceptable for regular software developers to reuse code… but it causes a lot of issues when that code is responsible for people’s funds.”
When asked if Kava would legally go after dForce, Kava commented that they wouldn’t. However, Kerr added,
“I don’t think their use of USDX was intentionally against us. I believe they just didn’t take the time to due diligence the name… With that said, dForce’s USDx is a shadow of what it was and isn’t traded on any major exchanges. I don’t see it being an issue for Kava.”
Conclusion
Security cannot be an afterthought, especially for an ecosystem that is building an improved financial infrastructure. Right now, DeFi protocols feel like they “move fast and break things,” however, what they should be doing is “move slow, and test things.” Since both the bZx and the dForce attacks were due to smart contract bugs, more DeFi projects should implement emergency procedures, conduct audits regularly, and roll-out progressive updates to patch issues in the older versions.
Perhaps, these attacks reveal that DeFi is a double-edged sword and the projects that are running and the ones that will launch can learn from the attacks and help build a stronger DeFi ecosystem.
Note: AMBCrypto reached out to dForce, lendf.me, and Mindao Yang for a comment, but did not receive one.






