Exchanges join DoJ in taking on Bitcoin, Ethereum-laundering Lazarus Group

A recent report released by Chainalysis revealed how U.S officials including the FBI, among other agencies, investigated the recent case of cryptocurrencies stolen by the Lazarus Group, a North Korea-affiliated hacker group.
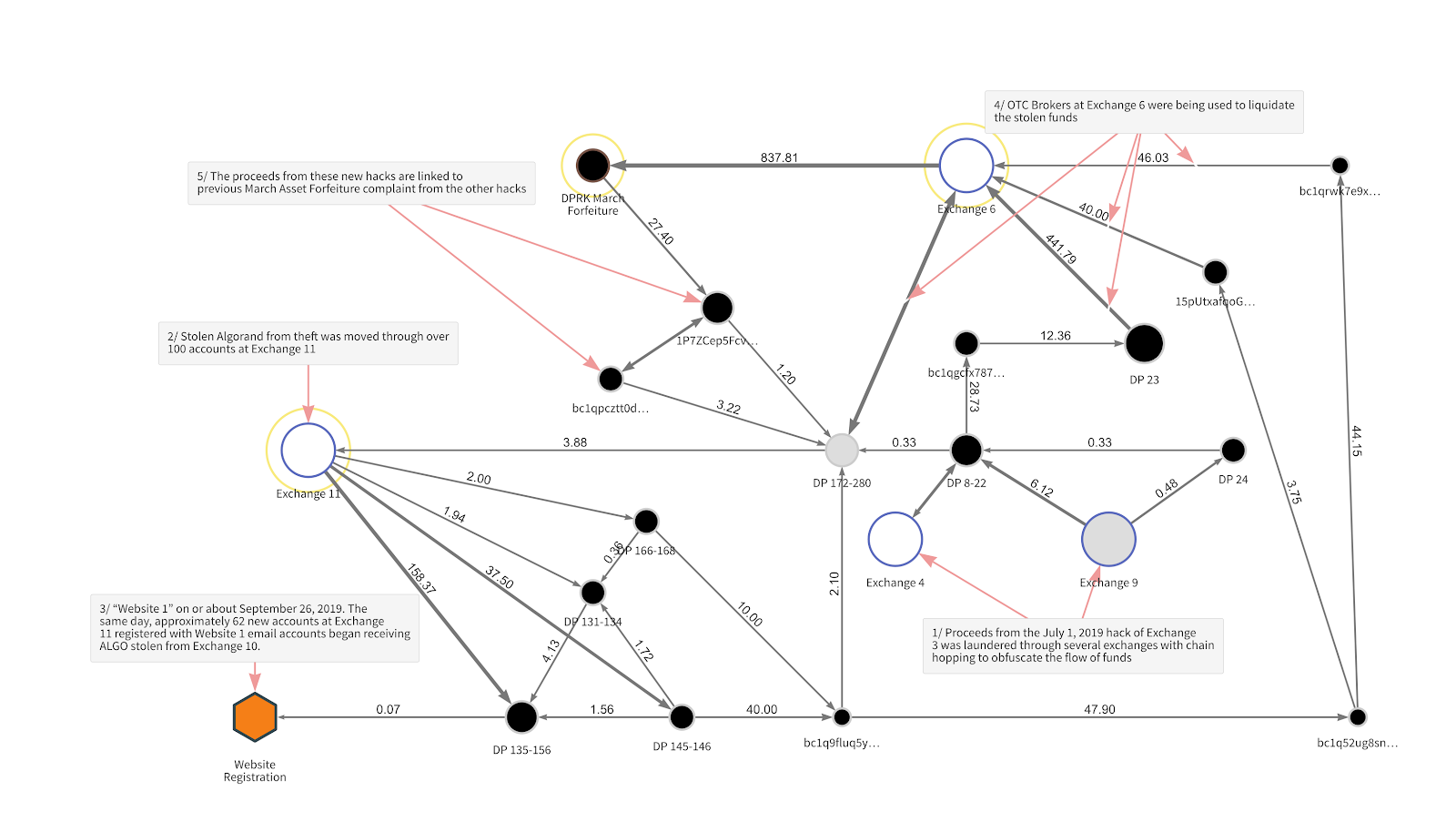
It was published soon after the U.S. Department of Justice forfeited 280 crypto-accounts involved in the laundering of approximately $28.7 million worth of cryptocurrencies following two crypto-exchange hacks. According to the report, investigators were able to keep up with the Lazarus Group, despite the fact that they tried to obfuscate their tracks by trying to liquidate the stolen funds via “chain hopping.”
The chain hopping technique includes trading funds for other types of cryptocurrencies to make it harder for law enforcement to trace the funds between blockchains. Moreover, the Lazarus hackers attempted to convert funds into Bitcoin and cash out through other services. Besides Bitcoin, the cryptocurrencies involved in these exchange hacks also included Ethereum and Algorand.
It should be noted, however, that chain hopping isn’t foolproof by any means, since it is often reliant on unregulated crypto-exchanges that do not rely on norms such as KYC checks.
According to Chainalysis, Lazarus Group moved large swathes of the stolen funds to OTC brokers to be converted into cash. Transactions are made over-the-counter or via OTC brokers when traders do not want to use a formal exchange. In this case, the OTC broker the hackers used was on Chainalysis’s list of “100 rogue” OTC brokers.
Chainalysis’s Reactor graph shown below traced the stolen cryptocurrencies.
Interestingly, the report also went on to explain that a few exchanges did assist in curbing the hackers’ efforts by pre-empting chain hopping patterns. In fact, when the Lazarus hackers moved their funds, some of these exchanges interrupted their transactions after exchange monitoring tools were able to identify incoming funds from an exchange hack.
This is a good sign since for long there have been cases where ill-coordinated efforts have had nothing to show for. In fact, it also indicates that exchanges are stepping up and keeping a vigilant eye on efforts to launder money internationally.
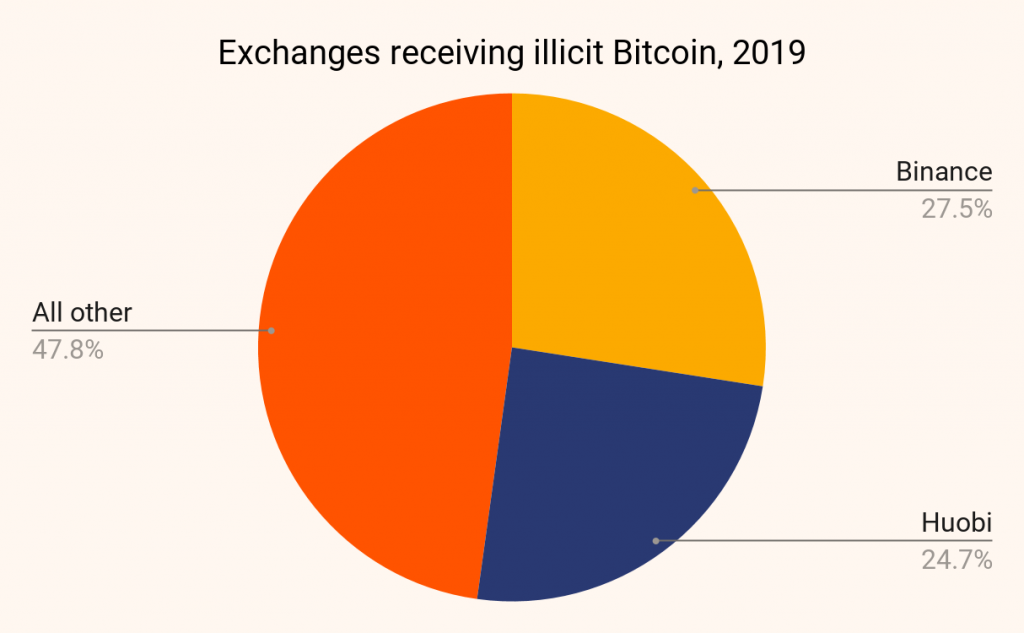
Here, it should be noted that the report in question did not explicitly mention the names of the exchanges that were involved. However, a previous study by Chainalysis had concluded that Binance and Huobi were among the two exchanges to have received the most funds (around $1.4 billion in Bitcoin) from criminal entities in 2019. Ergo, the probability that one of these two exchanges was involved is high.
Interestingly, both Binance and Huobi, two of the largest crypto-exchanges operating today, are subject to enforcing KYC or Know Your Customer regulations. One can therefore argue that the successful identification of these accounts and the exchanges’ assistance in doing so is a victory of sorts for those who have been clamoring for more crypto-regulations.
Before the DoJ’s announcement, the Lazarus Group was already in the news after F-Secure’s Threat Intelligence Team tracked the hackers’ latest attack to an advert on LinkedIn. Before that, the group was also believed to be responsible for an $81M ‘heist’ that crippled Bangladesh Bank.